Navigating the Shadows: Digital Forensic Analysis in Software Development Exposed
Unraveling the Mystique: Uncovering the Truth Behind the XZ Backdoor
In a tale that reads like a gripping cyberspace thriller, the open-source community has been rocked by a profound betrayal. The discovery of a backdoor in the xz/liblzma tarball reveals not only a breach of trust but also the dark side of anonymity in the world of free software development. As someone deeply entrenched in the realm of digital security through my work at DBGM Consulting, Inc., I find the orchestration and revelation of this backdoor both fascinating and alarming.
The Shadow of Anonymity: A Double-Edged Sword
Anonymity has always been a protective veil for many in the tech sphere, allowing talents to shine irrespective of the person behind the code. However, the case of Jia Tan, a long-time maintainer of xz who allegedly introduced this backdoor, starkly highlights the vulnerabilities inherent in this anonymity. As outlined by Rhea Karty and Simon Henniger, despite Jia’s contributions, little beyond a potentially false name was known about him, underscoring the risks when trust is betrayed within the community.
< >
>
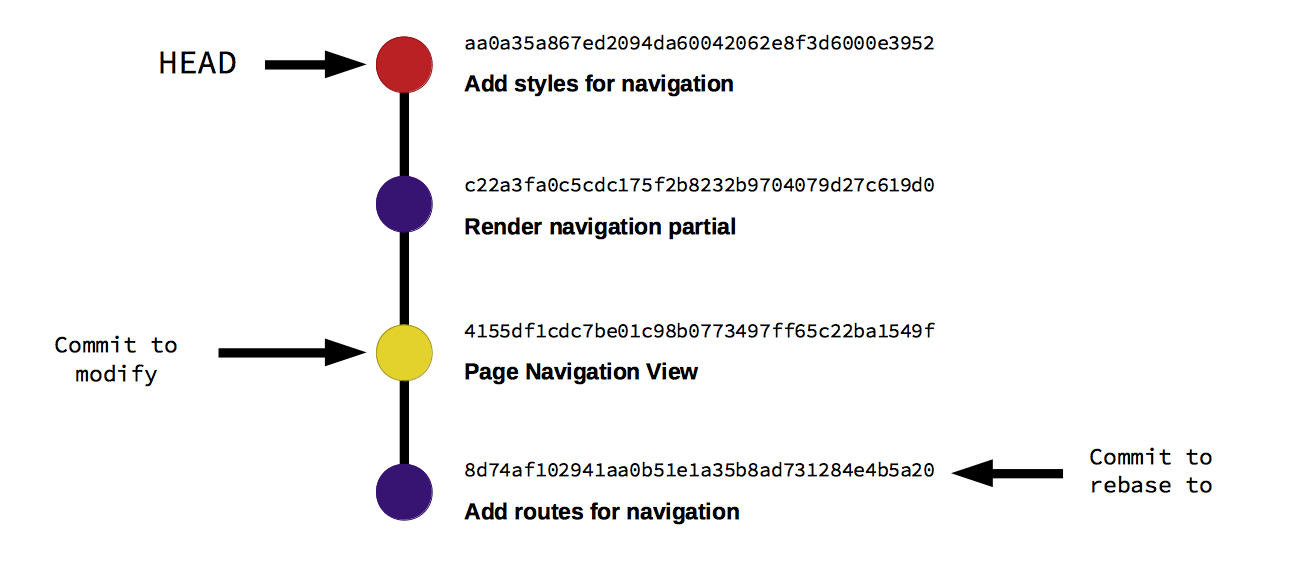
Timezone Forensics: A Clue to the Real Identity?
The intricate analysis of Git timestamps and coding patterns bring us closer to unveiling the truth. It’s a reminder of the sheer ingenuity required in digital forensic analysis, a field where I have leveraged my expertise in security to help clients understand and mitigate risks. The discussion on whether Jia Tan manipulated the timezone settings to conceal his actual working hours, potentially indicating his real geographic location, is a testament to the meticulous attention to detail required in our line of work.
< >
>
Decoding Patterns: The Behavioral Fingerprints
From my professional and academic background, including my tenure at Microsoft and my studies at Harvard University focusing on Artificial Intelligence, I’ve learned that patterns in data often tell a more compelling story than the data itself. The detailed investigation into Jia Tan’s commit habits and the improbable timezone shifts suggest a meticulousness and a forethought that belie a more significant intent. The methodology of analyzing work patterns and holiday schedules to deduce Jia’s probable location reflects advanced detective work in the digital age.
The Implications of Trust and Security in Open Source Development
This incident serves as a poignant reminder of the delicate balance between openness and security in the world of open-source software. While the collaborative nature of such projects is their greatest strength, it also exposes them to vulnerabilities that can be exploited by those with malicious intent. As a firm believer in the power of AI and technology to transform our world for the better, I view this event as a critical learning opportunity for the community to reinforce the security frameworks guarding against such breaches.
Securing the Digital Frontier: A Collective Responsibility
The backdoor uncovered in the xz/liblzma tarball is not just a technical challenge; it is a breach of the social contract within the open-source community. It underscores the need for vigilance, thorough vetting, and perhaps more importantly, fostering an environment where anonymity does not become a shield for malevolence. As we move forward, let us take this incident as a catalyst for strengthening our defenses, not just in code, but in the community spirit that underpins the open-source movement.
<
>
Reflecting on the philosophical musings of thinkers like Alan Watts, we are reminded that the journey towards understanding is fraught with challenges. However, it is through these challenges that we grow. The uncovering of the xz backdoor is a stark reminder of the perpetual battle between creativity and malice, highlighting the importance of community resilience and ethical dedication in the digital age.
As we navigate this complex landscape, may we remember the value of openness, not as a vulnerability, but as our collective strength. In shedding light on this deception, the open-source community demonstrates its enduring commitment to integrity and security—a lesson that resonates far beyond the realm of software development.
Focus Keyphrase: Digital Forensic Analysis in Software Development








Hi everyone, David Maiolo here. I wrote this article to share an insightful incident that strikes at the heart of the open-source community. Drawing from my experiences and the broader implications of such breaches, I hope to foster greater awareness and stronger security practices. The journey into digital forensics has never been more critical, as our collective efforts in transparency and trust define our digital age. Let’s learn and grow together in ensuring the sanctity of our open-source endeavors.
Interesting read, David. While I’m often wary of the direction AI and digital security are taking, it’s articles like these that offer a glimmer of hope. It’s fascinating (and a bit terrifying) to see how something as invisible as a backdoor can have such tangible impacts. Coming from an alarm company perspective, it reminds me of the constant battle between safeguarding and vulnerability. Also, being an anime fan, I can’t help but draw parallels to the intricate plots and moral lessons, much like in “Attack on Titan”. Here’s to hoping the digital community can stay one step ahead, just like the Scouts! Living in Florida now, but my skepticism and optimism were equally nurtured during my time in New York. Keep up the great work!